IP2 Network: A Deep Dive into Decentralized Peer-to-Peer Internet Infrastructure
The internet is evolving. What once depended heavily on centralized servers is now moving toward distributed, user-controlled systems. At the heart of this transformation lies the IP2 network—a peer-to-peer networking approach that challenges traditional internet architecture.

If you’re curious about decentralized networking, how peer-to-peer systems work, or why IP2 networks are becoming essential for Web3 and modern digital privacy, this guide will walk you through everything step by step, in plain English.
Understanding the Concept Behind IP2 Networking
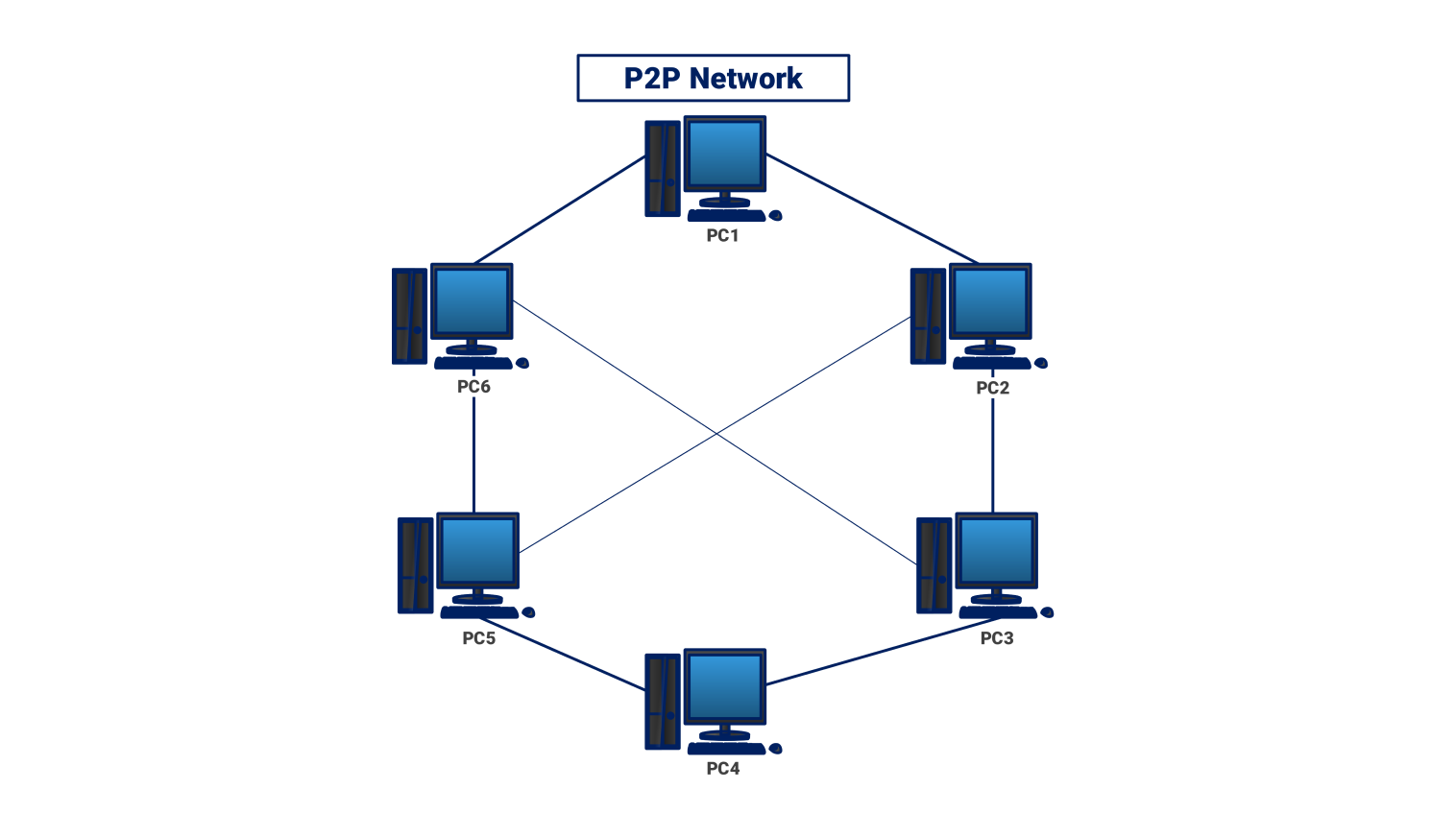
At its core, an IP2 network is a decentralized networking model in which devices communicate directly using the Internet Protocol (IP). Instead of relying on a central server to manage traffic, every participant—known as a node—can send, receive, and route data.
Imagine a conversation where everyone talks directly instead of whispering through one person. That’s the philosophy behind IP2 networking.
Why IP2 Networks Are Becoming Increasingly Relevant
As internet usage grows, centralized systems face serious challenges: server outages, data breaches, censorship, and rising costs. IP2 networks offer an alternative by distributing responsibility across multiple nodes.
This shift aligns perfectly with modern demands for:
- Digital privacy
- System resilience
- User autonomy
- Scalable infrastructure
Basic Internet Networking Explained Simply
To understand IP2 networks, it helps to grasp how traditional networking works. Every device connected to the internet has an IP address—a unique identifier that allows data to find its destination.
In classic networking, data usually travels from your device to a server, then back to you. This works, but it creates dependency on centralized infrastructure.
Limitations of Centralized Internet Systems
Centralized networking comes with built-in weaknesses:
- A single server failure can disrupt millions of users
- Data is stored in one place, making it a prime target for hackers
- Companies gain excessive control over user information
- Scaling requires expensive hardware upgrades
These issues pushed developers toward decentralized alternatives like IP2 networks.
The Shift Toward Peer-Driven Network Models
Peer-to-peer networking emerged as a solution to centralized bottlenecks. Instead of relying on one authority, participants share resources and responsibility.
IP2 networks take this idea further by using pure IP-based peer communication, enabling direct and efficient data exchange between nodes.
Defining IP2 Network in Technical Terms
An IP2 network is a distributed peer-to-peer system built on IP-based communication where:
- Nodes operate independently
- No central authority controls traffic
- Data routing is dynamic
- Network strength increases with participation
Each node is both a consumer and a contributor.
Distinctive Characteristics of IP2 Architecture
What sets IP2 networks apart?
- Decentralized control structure
- Direct node-to-node communication
- Distributed data handling
- Self-healing network behavior
These features make IP2 networks resilient and scalable.
How IP2 Networks Manage Communication
Communication in an IP2 network happens directly between peers. Once nodes discover each other, they establish encrypted channels and exchange data without intermediaries.
This reduces latency, lowers costs, and improves reliability.
Peer Discovery and Connection Formation
When a new node joins:
- It locates existing peers using discovery mechanisms
- Secure connections are established
- The node becomes part of the routing system
Discovery methods may include seed lists, peer exchange, or distributed lookup tables.
Dynamic Data Routing in IP2 Systems
Unlike static routing in centralized networks, IP2 networks dynamically select routes based on availability and performance. If one node fails, traffic is rerouted automatically.
This adaptability makes the network highly fault-tolerant.

Role of Nodes in an IP2 Network
Each node plays multiple roles:
- Data sender
- Data receiver
- Traffic router
Nodes contribute bandwidth, processing power, and storage, creating a collaborative system.
Distributed Storage and Data Availability
Instead of storing data on a single server, IP2 networks distribute fragments across multiple nodes. This ensures:
- Higher availability
- Reduced risk of data loss
- Improved redundancy
Even if some nodes go offline, data remains accessible.
Bandwidth Sharing and Resource Optimization
In IP2 networking, bandwidth is shared among participants. This collective resource pool improves performance and prevents congestion.
More users don’t slow the system down—they make it stronger.
Security Layers Within IP2 Networks
Security is critical in decentralized systems. IP2 networks typically rely on:
- End-to-end encryption
- Cryptographic identity verification
- Hash-based data integrity checks
These measures protect data from interception and tampering.
Comparing IP2 Networks with Centralized Models
Centralized networks depend on servers, while IP2 networks rely on peers. This difference affects everything from cost to reliability.
Centralized systems are easier to manage but fragile. IP2 networks require coordination but offer long-term resilience.
Performance Behavior Under Heavy Load
In centralized systems, increased traffic strains servers. In IP2 networks, additional users bring more resources, improving overall capacity.
This makes IP2 networking ideal for scalable applications.
Cost Efficiency of IP2 Infrastructure
Without the need for large data centers or constant server maintenance, IP2 networks dramatically reduce operational costs.
This makes them attractive for startups, decentralized platforms, and open-source projects.
Privacy Benefits of Decentralized Networking
Since IP2 networks avoid centralized data collection, users retain greater control over their information. There’s no single entity harvesting or monetizing user data.
This aligns well with modern privacy expectations.
Resistance to Censorship and Shutdowns
Decentralized systems are difficult to shut down because there’s no central control point. IP2 networks can continue operating even if parts of the network are blocked or restricted.
Potential Drawbacks of IP2 Networking
Despite their advantages, IP2 networks face challenges:
- Complex setup
- Variable performance depending on peers
- Risk of malicious nodes
- Regulatory uncertainty
These issues require careful design and monitoring.
Security Threats in Peer-Based Networks
Common risks include:
- Sybil attacks (fake nodes flooding the network)
- Data spoofing
- Unauthorized access
Strong cryptographic controls are essential to mitigate these threats.
Trust Models and Reputation Systems
To maintain integrity, many IP2 networks use reputation-based trust models. Nodes that behave reliably gain trust, while malicious actors are isolated.
Practical Applications of IP2 Networking
IP2 networks power many real-world systems, including:
- File sharing platforms
- Blockchain and cryptocurrency networks
- Decentralized applications
- Secure messaging services
- Distributed content delivery
These applications benefit from resilience and scalability.
Use of IP2 Networking in Blockchain Systems
Blockchains depend on peer-to-peer networking to distribute ledgers, validate transactions, and reach consensus. IP2 architecture enables trustless cooperation without central authorities.
Decentralized Applications and Always-On Services
Decentralized applications run across IP2 networks, ensuring uptime even if individual nodes fail. This makes them highly reliable compared to traditional apps.
Streaming and Content Distribution via IP2
IP2 networks allow users to share content directly, reducing server load and improving streaming performance through distributed delivery.
Relationship Between IP2 Networks and Web3
Web3 aims to decentralize ownership, identity, and control. IP2 networks provide the networking foundation that makes this vision possible.
Without decentralized networking, Web3 cannot function.
Comparison Between IP2 Networks and VPNs
VPNs rely on centralized servers to route traffic securely. IP2 networks distribute trust among peers, eliminating the need for a central intermediary.
Each serves different purposes, but IP2 offers deeper decentralization.
Basic Requirements to Build an IP2 Network
Setting up an IP2 network typically requires:
- Reliable internet connectivity
- Networking software
- Firewall and NAT configuration
- Encryption tools
Technical knowledge is helpful but not always mandatory.
Best Practices for Stable IP2 Performance
To maintain efficiency:
- Keep software updated
- Use strong encryption
- Monitor peer behavior
- Balance resource usage
These practices improve reliability and security.
Emerging Trends in Decentralized Networking
New developments include:
- Edge computing integration
- AI-assisted routing
- Decentralized identity systems
These innovations will enhance IP2 capabilities.
Impact of IP2 Networks on the Future Internet
IP2 networks are pushing the internet toward a more democratic model—one where users participate rather than merely consume.
This shift could redefine digital communication globally.
Clarifying Common Misunderstandings About IP2
IP2 networking is often misunderstood as illegal or unsafe. In reality, it’s simply a networking model. Its legality depends on how it’s used, not on the technology itself.
Final Thoughts on IP2 Network Technology
The IP2 network represents a fundamental evolution in Internet architecture. Removing centralized control, it enables privacy, scalability, and resilience. While challenges remain, its role in decentralized systems, Web3, and future internet infrastructure is undeniable.
As digital ecosystems continue to evolve, IP2 networking is poised to become a cornerstone of the next-generation internet.
FAQs
What is an IP2 network in simple terms?
An IP2 network is a decentralized peer-to-peer system where devices communicate directly using IP-based connections. Instead of depending on central servers, network nodes share data, bandwidth, and routing responsibilities collaboratively.
How does an IP2 network differ from traditional networking?
Traditional networking relies on centralized servers to manage communication. An IP2 network distributes control among peers, reducing single points of failure while improving scalability, fault tolerance, and resilience through direct node-to-node data exchange.
Is an IP2 network the same as peer-to-peer networking?
An IP2 network is a type of peer-to-peer networking that specifically uses IP-based communication. While all IP2 networks follow peer-to-peer principles, not every peer-to-peer system is strictly IP2 in design.
What are the main benefits of using an IP2 network?
Key benefits of an IP2 network include decentralization, enhanced privacy, reduced infrastructure costs, improved scalability, and resistance to censorship. As more nodes join, the network becomes stronger, faster, and more reliable overall.
Are IP2 networks secure to use?
IP2 networks can be highly secure when properly configured with end-to-end encryption, cryptographic authentication, and trust-based peer validation. However, security depends on implementation quality and effective protection against malicious or untrusted nodes.
What are common use cases of IP2 networks?
IP2 networks are widely used in file sharing platforms, blockchain systems, decentralized applications, secure communication tools, and distributed content delivery networks, where scalability, resilience, and reduced reliance on central servers are essential.
How does an IP2 network improve user privacy?
An IP2 network improves privacy by removing centralized data collection points. Direct peer communication and distributed data storage make it harder to track users, monitor activity, or exploit personal information compared to centralized networking models.
What challenges do IP2 networks face?
Common challenges include network latency, complex setup, security risks from malicious peers, and regulatory uncertainty. Managing decentralized systems often requires technical expertise to ensure stable performance and secure communication across distributed network nodes.
Is using an IP2 network legal?
Yes, using an IP2 network is legal. The technology itself is neutral, and legality depends on how it is used. Many legitimate applications rely on IP2 networking for decentralized communication and data sharing.
What is the future of IP2 networks?
The future of IP2 networks looks promising as demand grows for decentralized internet infrastructure. With the rise of Web3, blockchain, and privacy-focused technologies, IP2 networking is expected to play a key role in next-generation internet systems.